'One of the most sophisticated pieces of cyberespionage software' uncovered at Citizen Lab

An extremely advanced hack exploiting three iOS vulnerabilities in iPhones was recently uncovered by researchers at digital rights watchdog group Citizen Lab and mobile security company Lookout. Citizen Lab has informed Apple of the vulnerabilities, called zero-days, and a patch is available in the latest update, version 9.3.5.
SEE ALSO: Not even your vibrator is safe from data-mining, hackers prove
Emirati human rights activist Ahmed Mansoor first discovered the hack on Aug. 10, when he received suspicious-looking text from an unknown number: “New secrets about torture of Emiratis in state prisons," it read.
But Mansoor, who had been the victim of a serious hack via trojan from FinFisher and Hacking Team (they offer governments and law enforcement agencies so-called “offensive solution[s] for cyber investigations”) in 2011 and 2012, knew where to forward the message instead this time: to Bill Marczak, who works for Citizen Lab.

Image: citizen lab
Marczak and his colleagues found that the link actually led to a very complex piece of malware, which would've allowed the attacker full control of the iPhone. It was able to intercept every call or text, collect all emails or contacts and all of your data from apps like Gmail, Facebook, Skype, WhatsApp, Viber, etc., according to Lookout’s vice president of research Mike Murray.
“We realized that we were looking at something that no one had ever seen in the wild before. Literally a click on a link to jailbreak an iPhone in one step,” Murray told Motherboard. “One of the most sophisticated pieces of cyberespionage software we’ve ever seen.”
The malware came from a relatively unknown Israeli spyware provider called NSO Group. A report compiled by Marczak and his other colleague leading the project, John Scott-Railton, calls NSO a “cyber war” company responsible for selling Pegasus, a government-exclusive “lawful intercept” spyware product and other "extremely expensive spyware."
SEE ALSO: Edward Snowden: Equation Group hack is a warning from Russia to the U.S.
NSO is so secretive that it doesn't have a website, and its owners have rarely given an interview. They appear to be owned by a San-Francisco-based private equity firm, Francisco Partners Management LLC, according to Marczak and Scott-Railton's report. A 2015 Reuters article, however, suggested FPM wanted to sell NSO Group, valuing the firm at $1 billion.
Researchers infected a guinea-pig iPhone with NSO Group's malware, called Pegasus, and see how it affected the phone. A malicious website helps install the spyware, called "Agent," as an Anonymizer, which communicates back to a Pegasus Installation server over at the operator's location. So when the target clicks on the SMS link, the Anonymizer forwards the request to open the link back to the Pegasus server.
The server then looks at the target device's User-Agent header, and then checks to see if Pegasus has an exploit chain that supports the device. If there's a match, it begins to download on the target device. If the exploit chain fails to infect the target, it will redirect to a legitimate website set by the Pegasus operator, so it doesn't raise eyebrows.
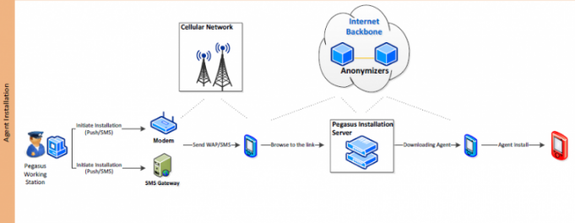
Image: hacking team emails/citizen lab
According to alleged NSO Group documentation, the firm felt that secrecy was key for Pegasus targets. "It is more important that the source will not be exposed and the target will suspect nothing than keeping the agent alive and working," it read.
Though the researchers were not able to trace the Pegasus anywhere else, they stressed the risk that NSO Group still poses for journalists and activists. And with the recent notorious hacks on FinFisher and Hacking Team, there's better potential than ever to dominate the government spyware market.
“The incentives just aren’t there for these companies like NSO to keep these tools out of the hands of serial abusers like the UAE,” Marczak told Motherboard. This is also the first sign of the rise of a new superpower in the spyware industry."

 Yahoo News
Yahoo News 