'They thought they were untouchable' - the hack that changed policing forever
They thought they were untouchable...but little did they know that law enforcement from around the world were monitoring their every move.
In April 2020, European law enforcement led by Dutch and French forces managed to hack the encrypted messaging service network EncroChat. The hack, one of the largest ever conducted by authorities, saw malware secretly planted into the system which allowed forces from around the world access to millions of once-hidden messages.
The messages gave police forces a unique access like they had never seen before. Criminals openly talked about everything from their drug and firearms deals to the organisation of murders. On June 13 2020 the hack was made public, with EncroChat advising its users to power down and dispose of their phones.
READ MORE: Teacher found guilty of having sex with pupils
READ MORE: Brutal steps rival Liverpool and Manchester gangs took to climb criminal ranks
The public announcement forced the hand of law enforcement, who soon cashed in on the intelligence gold mine. Since then, around 1,500 offenders have been convicted using EncroChat data as evidence in the UK. That data acquired from the hack has been used to remove some of the most dangerous criminals from the streets.
Last week, the ECHO could finally reveal the role Vincent Coggins played in Merseyside's criminal underworld as the head of a menacing organised crime group (OCG) called the Huyton Firm. Coggins was unmasked as the leader of the gang in 2020 following the EncroChat hack, but his involvement could only be made public at the culmination of the trial of one of his criminal associates.
But what was EncroChat, and how did it become the downfall of criminals around the world?
What was an EncroPhone?
The once top-secret messaging system - used by drug dealers, gun runners and gangs - operated on customised Android mobile phones. Accessed by a secure password, a user on the platform was given a unique 'handle', typically made up of a noun and an adjective.
However, the ECHO understands EncroChat offered a bespoke service whereby users could pay a fee to choose their own name. In some cases, the handle was eventually used as a stepping stone for the authorities to identify the person behind it.
Criminal organisations used the expensive phones, which cost between £1,200 and £1,500 for a six-month contract, to organise their criminal activities without fear of their messages ever being seen by law enforcement. The EncroChat system could "guarantee anonymity" for its users, according to the company behind it.
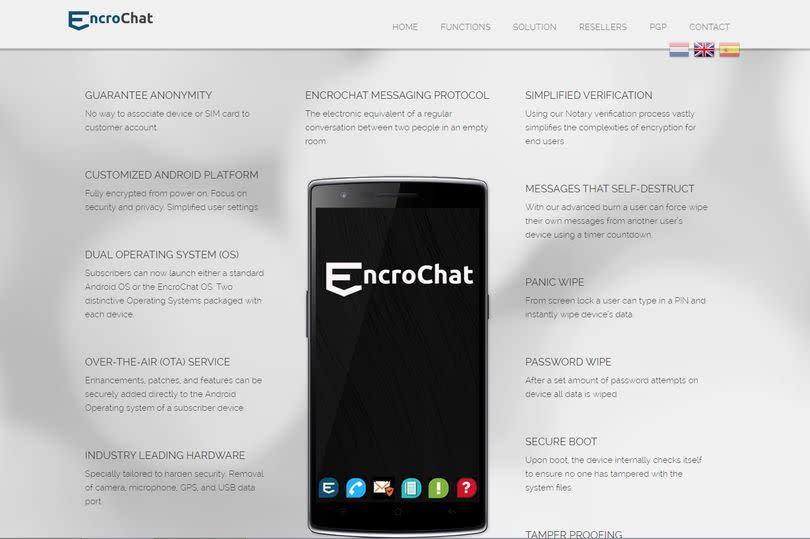
The phone had a number of security features that included encrypted chats, phone calls and notes. There was also panic wipe, where all the data on the device could be deleted by entering a four-digit code from the lock-screen. The phones could also have its camera, microphone and GPS chip removed.
Who was behind EncroChat?
The identities of the people behind the encrypted service are not known. The National Crime Agency (NCA) told Sky News that the company itself has not been accused of criminal activity, but its platform was used by criminals.
However, Dutch journalist Jan Meeus claimed a Dutch organised crime group was involved and financed the developers. Following the hack, Vice reported that someone responded via an email associated with EncroChat to tell the website it was shutting down.
They said: "Our main priority has always been our customers integrity and security, and when we no longer can guarantee that, we have no other choice than to shut down the service even if it destroys our business."
How did the authorities hack it?
The encrypted messaging system came to the attention of French authorities in 2017, around a year after the EncroChat platform first came online. Sky News reported that the French police discovered that EncroChat was operating from servers based in the city of Roubaix, France and were eventually able "to put a technical device in place" which allowed them to access the encrypted messages sent over the network.
In February 2020, French and Dutch authorities revealed they had developed software that could obtain data from EncroChat. The hack, implemented via an update, collected usernames and messages on the handsets, as well as the location they were used in through Wi-Fi hotspots.
This information was soon shared with the UK authorities and by April 2020, the NCA had access to millions of texts and hundreds of thousands of images linked to handles in the UK. Under the codename Operation Venetic, the agency began to analyse the huge amount of data.
Operation Venetic
Operation Venetic is a UK-wide probe led by the NCA working in partnership with every police force in the country. Of the 60,000 worldwide users, the NCA said around 10,000 of the handles were linked to the UK. The former NCA director of investigations said at the time: "These are people who are causing vast amounts of misery and harm across the UK.
"These are what we would call iconic untouchable, these are people that have worked with impunity and evaded law enforcement and now we have been able to get inside and see exactly what they are doing." As a result of the infiltration, in the early days after the hack was made public, UK police arrested 746 individuals, including major crime bosses, intercepted two tonnes of drugs, worth around £100m, and seized significant quantities of cash and weaponry including sub-machine guns.

According to national figures released by Greater Manchester Police, law enforcement agencies have now made 3,100 arrests, convicted 1,500 offenders, recovered over nine tonnes of class A drugs and £84m in cash and seized 3,500 rounds of ammunition.
In 2022, the first people convicted of conspiracy to murder using EncroChat data were jailed. Frankie Sinclair, of Cardiff, and Paul Fontaine, of north London, were jailed for life with a minimum of 18 years after a plot to buy a handgun to kill a gang rival was uncovered.
Many of those convicted incriminated themselves by sending personal details and pictures to other handles. In some staggering instances, criminals have been convicted because pictures of their hands holding drug blogs have been matched with their fingerprints.
EncroChat on Merseyside
Merseyside Police launched Operation Aquarium - the force's overarching response to the EncroChat hack. Of the 10,000 handles in the UK, hundreds were thought to be on Merseyside. In the first year following the hack, over 100 suspects were arrested, with investigators warning they had the username of every EncroChat device thought to have been based on Merseyside.
Merseyside Police's head of investigations, Detective Chief Inspector Mark Kameen, who went on to lead the probe into the murder of Olivia Pratt Korbel said on the one year anniversary of the hack: "We have hundreds of people still to go and speak to and arrest. We are working the data. That takes a lot of time. But we will get to every single one. We will come knocking for you and you are likely to face prison sentences similar to those already handed out."
Some of the first arrested and charged in Merseyside using EncroChat data was Vincent Coggins and his associates Paul Woodford, Michael Earle and Edward Jarvis. Coggins used the handle “moonlitboat”, while Earle, Jarvis and Woodford went by the handles "bladehedge", "Softherb" and "kingwasp" respectively.
The men were arrested and charged as part of the North West Regional Crime Unit's (NWROCU) 'SubZero' operation, which marked some of, if not the first arrests using the EncroChat data as evidence. The Huyton Firm men were implicated in a drug and blackmail conspiracy after one of their stash houses was raided.

The men were involved in criminality for decades before the plot, but the data acquired through the hack provided the evidence the law authorities needed. All but Jarvis pleaded guilty to the offences, and gang boss Coggins was jailed for 28 years. After them the floodgates opened and a number of Merseyside's key players were incriminated.
Since then the likes of Thomas Maher, who used the handles "Satirical" and "Snacker" to smuggle £1.5m of drugs into the country, have been jailed. Maher was jailed for 14 years and eight months, while dealers John Barton and Daniel Rushworth, who discussed the sales of drugs and the brokering of the gun, were jailed for 21 and 16 years and four months respectively. To see just some of the Merseyside criminals who used EncroChat click here.
Was the EncroChat hack legal?
While most convicted of EncroChat offences have pleaded guilty believing there to be too much of a weight of evidence against them, some have fought their charges in court by arguing the evidence wasn't lawful. There have been a number of cases that have questioned if the evidence can lawfully be used.
Computer Weekly, who has expertly reported on the EncroChat hack since the beginning, said under UK law, phone calls or data intercepted during the course of transmission are prohibited from being used as evidence and cannot be referred to during a court hearing to protect the methods used by law enforcement.
The restriction, however, does not apply if the same data is obtained from storage in an electronic device through a hacking operation. European authorities have refused to disclose how the infiltration operation was carried out citing defence secrecy. Prosecutors have argued the messages were obtained from electronic storage, but defence lawyers have argued messages were obtained during the course of transmission.
In March this year, a case involving a former Liverpool FC youth star, known as Embossed II, was the "lead case" in the long-running argument. Jamie Cassidy, his older brother Jonathan and business partner Nasar Ahmed pleaded guilty to the offences before them after Judge Nicholas Dean, the recorder of Manchester who also presided over the trial of Coggins' associate Jarvis, found messages could be lawfully used.
Computer Weekly reported that in a written ruling, Judge Dean said there was no doubt that a vast amount of data was retrieved, and that the material, if admissible, implicates those proved to have used the handsets to send and receive messages in serious crime. He said: "Whatever else, this is not a case of flawed or corrupted software giving the appearance of individuals being involved in criminal activity."
What next?
Criminal courts around the country are still hearing dozens of EncroChat hearings a week, showing the sheer scale of criminality involving the messaging platform. Before EncroPhones, criminals used other encrypted messaging services, such as Blackberry. It's highly likely that the underworld will seek out private network alternatives to EncroChat to continue their illicit businesses, if they haven't already.
However, the success of the EncroChat hack and the impact it's had on removing some of the UK gangland's biggest players will undoubtedly mean their next steps are taken with more caution than before.
Don't miss the biggest and breaking stories by signing up to the Echo Daily newsletter here.

 Yahoo News
Yahoo News 
