U.S. Firms Hired North Korean IT Workers Posing as Americans
After an investigation that spanned at least a half-decade, the feds have interrupted a scheme that exploited online freelance job sites “to circumvent U.S. sanctions and earn money for North Korean government entities involved in ballistic missile research and development.”
On Wednesday, the FBI announced the seizure of 17 web domains North Korea allegedly set up to masquerade as legitimate U.S.-based tech firms. The feds also seized at least $1.1 million held in online accounts by North Korean agents pretending to be Americans.
An FBI search warrant affidavit obtained by The Daily Beast provides insight into how North Korean agents allegedly obfuscated their true identities to get remote IT jobs in the United States, generating millions of dollars for Pyongyang.
One shadowy crew of gig workers operated out of a 24-floor hotel in Yanji, China, and funneled their illicit cash through a North Korean front company in Vladivostok, Russia, and through a series of bank accounts in China, Nigeria, Ukraine, Pakistan and India, the warrant states. Yanji is the seat of Yanbian Korean Autonomous Prefecture in China’s Jilin Province, wedged between the North Korean and Russian borders and home to an ethnic Korean population that comprises up to half of the city’s 400,000 residents. Another group worked out of Dalian, a Chinese port city with a large North Korean presence and a crucial node in Pyongyang’s sanctions-evasion network.
The organization had a clearly defined hierarchy, with individual workers assigned to a group leader, and those leaders reporting up to a delegation leader, the affidavit goes on. They used non-Korean names to carry out the ruse, and ultimately claimed to have built websites for, among others, a New York City neurobiologist, a San Francisco venture capitalist, and a software developer in New Hampshire.
“I’m as shocked as you are,” Kristie Powell, a small business owner who unwittingly hired a North Korean IT worker, told The Daily Beast, declining to comment further.
The FBI first became aware of one of the front companies, Eden Programming Solutions, in Oct. 2020, according to court documents. The company’s sleekly-designed website advertised services including website and app development, and made North Korean government agents appear to be legitimate American remote workers for hire. Eden, which listed a business address in Walnut Creek, California, had an account on one freelancing website which showed they had earned $422,000 since Oct. 2017, the FBI found. (The FBI later found the address was vacant.)
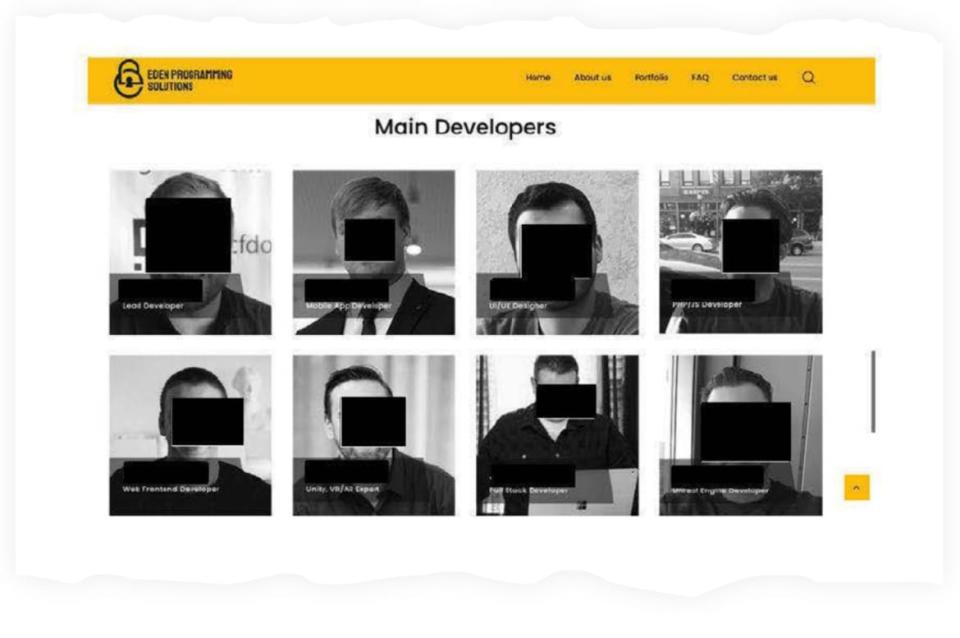
Eden Programming Solutions’ website featured a phantom “staff” of people who did not actually work there.
The website setup was paid for with a Mastercard out of Ukraine, the affidavit states.
“Our qualified team of interface designers and software developers is always ready to create something unique to you,” the company told potential clients, according to an archived version of Eden’s website.
On its site, Eden claimed to be an award-winning company with 21 employees who had developed 25 apps. Black-and-white portraits showed eight of the company’s “main developers.” In reality, these people did not exist, according to the FBI.
At least one of the pictures used by Eden to depict a “web frontend developer” was taken from the social media account of a Spanish influencer named Christian Bresser, a Daily Beast analysis found.
Eden was only one of 17 such front companies identified by the FBI in a separate seizure warrant reviewed by The Daily Beast. Another, called Xinlu, claimed to have a team with 20 years of software development experience.
“Meet your new best friends, our gurus,” the website read, above photos of fake employees.
The North Korean IT workers recruited targets on Fiverr, asking them to rent out their Upwork accounts for a fee. The North Koreans’ payment would then be routed into a PayPal or Payoneer account usurped using the same method, according to the FBI.
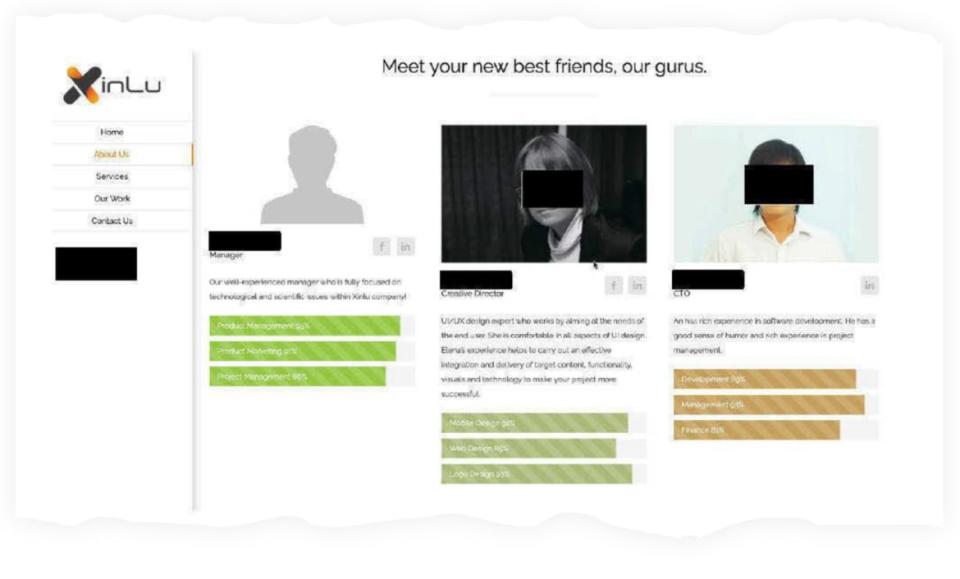
“Meet your new best friends, our gurus,” one of the North Korean false-front websites told prospective customers.
Ultimately, the proceeds were put toward Pyongyang’s weapons programs, the feds say.
Fiverr, Upwork, PayPal, and the other platforms used surreptitiously by North Korean agents are not accused of any wrongdoing. Payoneer responded to a request for comment on Wednesday, with a spokesperson saying the company was “not at liberty to comment on investigations conducted by law enforcement agencies,” but that it maintains a “strong commitment to anti-money laundering [practices] and the protection of the global financial system.”
An Upwork spokesman, Aaron Motsinger, also declined to comment on the specific allegations but said Upwork “invests heavily in developing cutting-edge detection tools, strong relationships with law enforcement agencies (including the FBI), and an industry-leading team of skilled professionals–comprised of over 300 global team members spanning payments/anti-money laundering, legal, intelligence, investigation, and machine learning detection–that is focused on ensuring our platform and customers stay as safe as possible while finding, catching, and shutting down fraudulent activity of this kind.”
The operation generated at least $1.5 million, FBI Special Agent in Charge Jay Greenberg told The Daily Beast. Greenberg, who oversees the St. Louis Field Office and supervised this investigation, said the bureau is “very confident saying that at a bare minimum, there are thousands and thousands of these North Korean IT workers who are part of the global job market.”
Greenberg said the issue is so widespread that any U.S. business owner who is not yet aware of it is likely already impacted.
“Chances are that they have been victimized in this scheme,” he said. “Chances are they’ve given somebody access, or they just didn’t know the kind of due diligence that they should perform,” Greenberg said.
The investigation that led the FBI to Eden Programming Solutions began in Aug. 2019.
That month, agents interviewed an unnamed Upwork user identified as “Individual 1,” according to the search warrant affidavit, which does not specify where the meeting took place. Greenberg declined to provide more details about how agents homed in on Individual 1 other than to say, “Cyber is a team sport.”
Through Individual 1, investigators uncovered a Skype account under the name “Chris Nohara,” along with email accounts “utilized by an individual who works for Yanbian Silver Star, a.k.a. China Silver Star”—the North Korean front company in Vladivostok. This person is identified in the affidavit as “Individual 2.”
Yanbian Silver Star, which the feds claim also goes by a multitude of other names, was blacklisted in 2018 by the U.S. Treasury Department, which says the entity is run by a sanctioned North Korean national, Jong Song Hwa. As of mid-2018, Yanbian Silver Star had earned “millions of dollars” from freelance IT projects, according to Treasury officials. A second firm, spun off from Yanbian Silver Star, was also located in Russia and run by North Koreans, who brought in “hundreds of thousands of dollars” in under a year, Treasury said.
A news report of a North Korean rocket launch, seen on South Korean TV.
The person calling themselves Chris Nohara asked to use Individual 1’s Upwork account and computers, offering to pay $100 per month per laptop. Whenever “Nohara” got paid for a freelance job, Individual 1 would get 15 percent as a fee and the rest went to Nohara’s accounts in mainland China.
Ultimately, Individual 1 had four laptops in their home in the United States, which the North Korean agents used through remote access software, the FBI says.
According to the affidavit, Nohara’s pitch to potential U.S. clients went like this: “Hi, Thank you for your interesting [sic]. As I mentioned, I want to loan your upwork account [sic]. You will have to create upwork freelancer account under your name and photo. And I will have access of that account and will use via team viewer. I need 24/7 Teamviewer access. I will pay you money each month. Are you still interesting [sic]? Thank you.”
Greenberg told The Daily Beast this kind of set-up is common in these sorts of schemes, and sometimes people involved do not even realize they are part of a wider criminal conspiracy. On the other hand, if someone in the U.S. was knowingly participating in the North Korean scam—no evidence of this has emerged to date—then they “certainly could face consequences,” Greenberg said.
Nohara was good at keeping up appearances, using a phone number with a Gainesville, Florida area code to text with Individual 1, the affidavit states. But Nohara’s rudimentary operational security was no match for the subpoena power of the U.S. government. Agents obtained his emails and chats with coworkers in Yanji, which were reviewed and translated from Korean to English by FBI linguists.
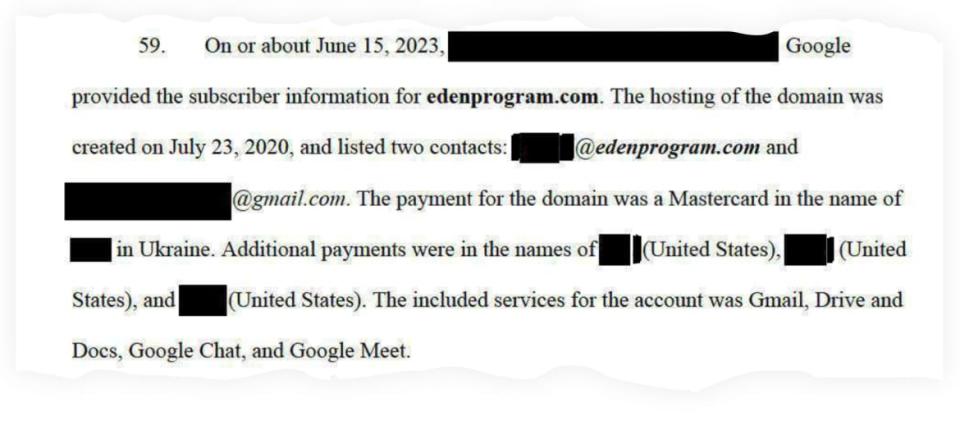
The Eden Programming Solutions false-front website was set up by North Korea using a Mastercard registered in Ukraine, according to the FBI.
The emails offer insight into how the agents operated. They show the team discussing work they were doing for clients, arranging to meet up for cigarette breaks, and talking about finding Nohara profile picture that did “not look Asian,” according to the affidavit.
The team went to great lengths to conceal their identities, according to the FBI. Seized emails show one email account operated by the group was used to pay for multiple fake U.S. drivers licenses, passports, and bank statements, according to the warrant. The group also maintained a cloud storage drive containing resumes, job descriptions, interview scripts and spreadsheets cataloging the revenue, the FBI found.
They continued to run up against one problem: what to do when a potential employer asked to interview them on camera. In one instance, a member of the crew told an unidentified hiring manager they couldn’t be on a video call because they didn’t have a webcam.
“The FBI believes this chat was for a freelancer job interview and the user… did not want to use their camera as their appearance would not match their freelancer persona,” the affidavit states.
To bypass this issue, the North Korean agents would sometimes “either pay or deceive non-North Koreans to interview for jobs for them," the FBI concluded. “These non-North Koreans may not be aware that the IT workers are North Korean.”
Yet, there were still a number of dead giveaways, according to the affidavit. One of the North Korean agents used “PY” as the answer to a security question for one of their email accounts, which the affidavit points out is the abbreviation for “Pyongyang.” In August 2020, someone checked the balance in one of the North Korean bank accounts from an IP address registered to North Korea’s government-run telecom agency, the affidavit states.
In August 2020, an FBI undercover operative in the St. Louis area made direct contact with Nohara, who said he wanted to connect to the agent’s laptop remotely, according to the affidavit. This would “provide [him] with the appearance of residing in the United States and the ability to avoid using a Virtual Private Network (“VPN”) IP address which might be blocked by Upwork,” it says.
Once Nohara linked his computer with the FBI laptop, agents were able to monitor his activities from afar, in real time, without his knowledge.
The secret backdoor into Nohara’s computer quickly paid dividends, according to the affidavit. At the beginning of September 2020, FBI agents observed Nohara shifting money around using an account linked to one of his dozens of Gmail addresses. They subsequently watched him log in to the FBI-monitored laptop and communicate with an account agents would soon ID as the North Korean team leader, according to the affidavit.
Using a handle that mimicked the name of a legitimate Swiss software company, the team leader—whose name The Daily Beast has agreed not to share—led group chats in which he requested “weekly work and PayPal reports from the group, discussed delegation meetings, assigned work responsibilities regarding the cleaning and cooking of meals, requested money be provided to him so he could send it home, provided guidance to the team related to COVID-19 in Yanbian, specifically to avoid taxis, requested a group picture at the Kairos Hotel (open source identified a Kairos Park in Yanji, Jilin, China, the known location of the group), and other administrative type requests,” the affidavit states.
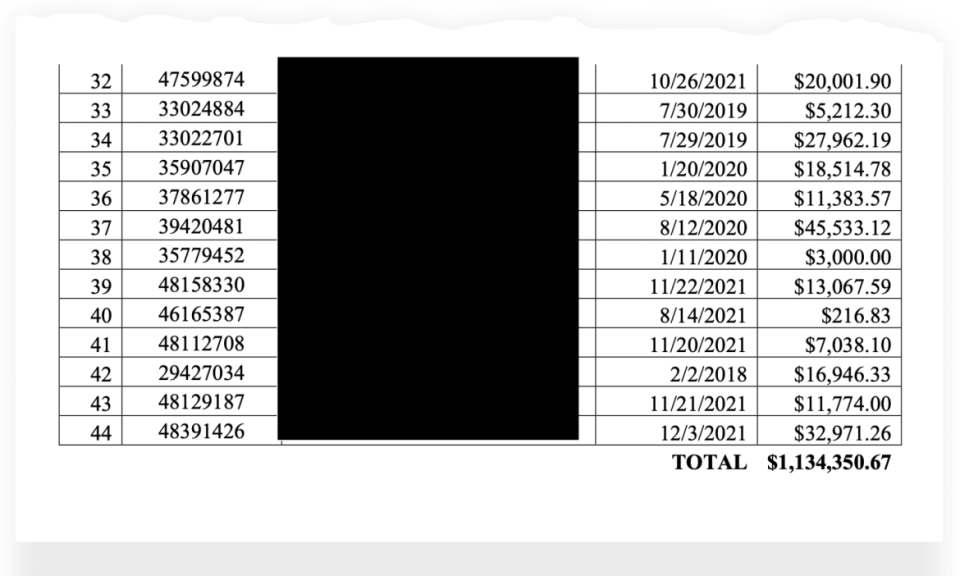
The North Korean IT workers brought in and laundered at least $1.1 million before the FBI seized their accounts.
During the first few months of 2021, the FBI obtained subscriber records for various other online accounts maintained by the team leader, according to the affidavit. It says the accounts further tied him to the conspiracy, corroborating information provided by Individual 1, linking the team leader directly to the administration of the Eden Programming Solutions domain, and to payment accounts associated with the “freelancer personas.”
As of Christmas Eve 2021, Nohara’s laptop was still being used to log into the accounts flagged by the FBI as being under North Korean government control, the affidavit states. On Wednesday, the years-long investigation finally came to a conclusion.
The issue has been ongoing, and an advisory issued last year by the State Department, Treasury Department, and FBI warned Americans about potential overtures by North Korean IT consultants in disguise. The uptick in remote work due to the COVID-19 pandemic also served to juice the North Koreans’ ability to get off-site jobs in western nations, according to Greenberg. He said that hiring managers should always insist on video interviews with job candidates to confirm they are who they say they are.
Many North Koreans are working in China, but still under tight control by minders from Pyongyang and not freely moving about, Greenberg said, noting that someone conducting a video interview might well pick up cues from a candidate that something is slightly off in that regard. And if someone applying for a project says they’re in Nashville, for example, but it’s nighttime when it should be daytime, or they’re in a location that is obviously overseas, Greenberg said it gives a company “a runway to figure that out sooner in the process.”
Most North Korean IT hires have gone undetected by employers, according to Greenberg.
“So we would really encourage all the companies out there… to take a hard look at how they’re onboarding their IT workers,” he said.
This latest crackdown won’t stop North Korean subterfuge altogether, Greenberg acknowledged, but called it “a disruption of their functional capabilities… [that will] take quite a bit of money out of their hands.”
Get the Daily Beast's biggest scoops and scandals delivered right to your inbox. Sign up now.
Stay informed and gain unlimited access to the Daily Beast's unmatched reporting. Subscribe now.

 Yahoo News
Yahoo News 
